The Misleading Dilemma: How Instant Technology Brings Together Privacy and Protection
- Malaysia’s MCMC collaborates with tech giants to implement eKYC protocols for under-16s, prioritizing privacy under data protection laws. - Traditional document-based verification risks data breaches, with 2025 IBM report citing $4.4M average breach costs. - Privacy-first solutions like real-time biometrics verify identity without storing sensitive data, aligning with KYC/AML standards. - Global challenges include $2T annual money laundering and $10B U.S. costs from underage social media access, driving
The Dilemma of Age Verification and Privacy: How Document Uploads Backfire—and What Solutions Are Emerging Globally
The struggle to find equilibrium between privacy and security in digital identity checks has intensified, as regulators, companies, and users debate how to ensure safety without sacrificing personal data. Central to this issue is the increasing use of document uploads for age verification—a method critics say puts private information at risk and doesn’t effectively counter modern fraud. In response, governments and technology companies are piloting new approaches that safeguard privacy while maintaining robust security.

Malaysia is taking the initiative on this front. The Malaysian Communications and Multimedia Commission (MCMC) has revealed plans to consult with
Still, relying on documents for verification brings significant dangers. Traditional processes—like uploading identification or answering security questions—concentrate sensitive information, making breaches more likely. According to a 2025 IBM study, the typical data breach now costs $4.4 million, highlighting the steep financial and reputational risks. Users are caught in a bind: strict checks can prevent fraud but undermine confidence, while weaker controls open the door to misuse.
Privacy-centric alternatives are now gaining traction. Rhon Daguro, CEO of AuthID, suggests that the supposed trade-off between privacy and security can be overcome with tools such as live biometric authentication. Unlike document uploads, these systems use a “verify,
The need for these advancements is pressing. The United Nations estimates that $2 trillion is laundered globally each year, much of it enabled by inadequate digital verification. In the U.S. alone, underage access to social media and financial tools is a $10 billion issue, based on 2023 FTC figures. By embracing privacy-focused systems, organizations can satisfy regulatory requirements and build user trust—an essential goal as governments worldwide strengthen age-check laws to safeguard children.
Moving forward, cooperation is essential. Malaysia’s MCMC talks highlight the necessity for regulators and platforms to synchronize technical and legal frameworks. For individuals, the takeaway is clear: privacy and security are not opposing forces, but rather, they work together to create a safer digital environment.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
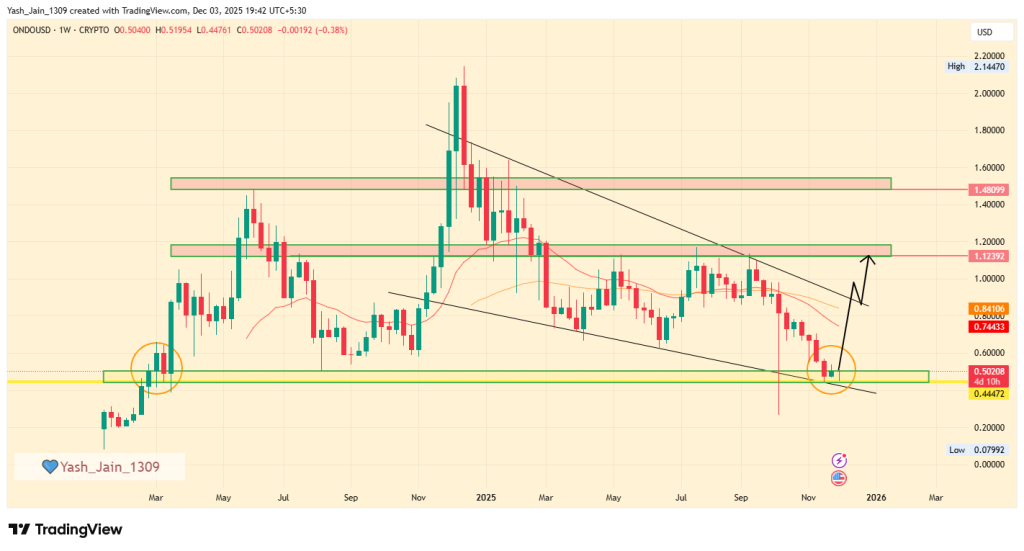
ONDO Price Eyes 120% December Rally as Falling Wedge Pattern Strengthens
Crypto News Today: SEC Stops ProShares From Launching XRP and Other Leveraged Crypto ETFs
Bitcoin Leverage Liquidation and Potential Dangers of Excessive Exposure in 2025
- 2025 crypto market saw $1B+ leveraged liquidations as Bitcoin fell from $126k to $92k amid Fed policy uncertainty and geopolitical tensions. - Retail traders suffered disproportionately from 10x-20x leverage during price corrections, while institutions used ETFs and hedging to mitigate risks. - Derivatives market vulnerabilities exposed include liquidity crunches, algorithmic feedback loops, and cross-market contagion risks via crypto-treasury overlaps. - Post-2025 lessons emphasize 3x-5x leverage caps,

The Recent Fluctuations in the Solana Network and What They Mean for Blockchain Investors
- Solana's 2025 volatility highlights risks for blockchain investors from market psychology and infrastructure flaws. - November 2025 saw 6.1% price drops driven by leverage, Fed rate uncertainty, and plummeting on-chain activity metrics. - $3.1B in DeFi losses from smart contract exploits and AWS outage risks exposed technical vulnerabilities despite decentralization gains. - Investors must balance sentiment indicators (fear/greed index) with technical metrics (TVL, DEX volume) to navigate Solana's instab