The UXLink exploit was a multisignature wallet breach that allowed attackers to mint billions of unauthorized UXLINK tokens, crashing price and prompting a new audited Ethereum contract. Immediate fixes include timelocks, hard-coded supply caps, renounced mint privileges and independent audits to prevent repeat incidents.
-
Multisig compromise enabled mass minting, slashing UXLINK value.
-
Project deployed a new audited Ethereum contract and removed mint-burn functionality.
-
Estimated losses range from ~$11M to over $30M; security hardening recommended.
UXLink exploit coverage: multisig breach, estimated losses, new contract fixes and practical smart-contract hardening steps. Read how projects can secure tokens now.
FearsOff CEO Marwan Hachem said the incident underscores the risk of retaining centralized control in projects that present themselves as decentralized.
Decentralized social platform UXLink said Wednesday it deployed a new Ethereum contract after a multisignature wallet exploit allowed attackers to mint billions of unauthorized tokens and collapse the native token’s market value.
UXLink confirmed the new smart contract passed a security audit and will go live on the Ethereum mainnet. The replacement contract removes the mint-burn function to eliminate the risk of arbitrary supply expansion.
The project confirmed the breach on Tuesday and said a significant amount of crypto was moved to exchanges. Loss estimates vary by source: Cyvers Alerts reported at least $11 million stolen, while security firm Hacken estimated losses in excess of $30 million.
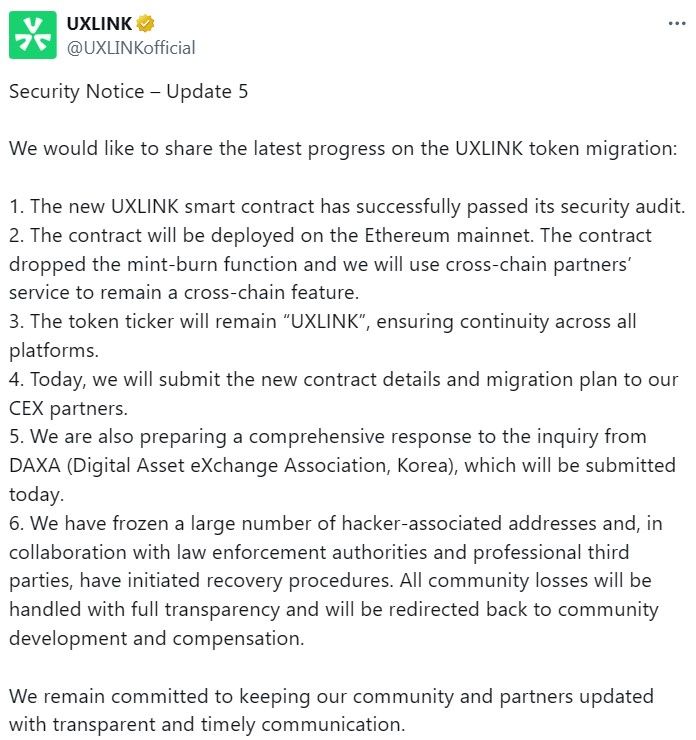
Source: UXLink
What is the UXLink exploit and what happened?
The UXLink exploit was a multisignature wallet compromise that allowed attackers to execute a delegate call vulnerability, take administrative control and mint billions of UXLINK tokens, causing the token price to fall roughly 90% from $0.33 to $0.033.
How did the attacker gain control of the multisig wallet?
According to analysis and expert commentary, the breach exploited a delegate call vulnerability inside the multisig setup. That weakness permitted arbitrary code execution and effectively bypassed intended signer controls, enabling unauthorized minting and administrative actions.
What are the estimated losses and measurable impact?
Estimates differ: Cyvers Alerts reported at least $11 million in stolen funds, while security firm Hacken estimated losses exceeding $30 million. The attacker initially minted approximately 2 billion UXLINK tokens and, by some estimates, created nearly 10 trillion tokens overall, driving a severe market crash.
Why did this failure happen and what safeguards were missing?
Expert Marwan Hachem of FearsOff pointed to design flaws: a multisignature wallet not hardened against delegate call exploits, lax mint controls and no code-enforced supply cap. Those gaps allowed centralized privileges to be abused once the multisig was compromised.
How can projects prevent similar breaches?
Technical and operational safeguards can significantly reduce risk:
- Add timelocks: introduce 24–48 hour delays for sensitive actions so the community can detect anomalies.
- Hard-code supply caps: enforce maximum supply within contract logic to block unauthorized minting.
- Renounce mint privileges: remove minter roles after launch so insiders cannot mint tokens later.
- Audit multisig setups: audit multisig implementations and related delegate calls as thoroughly as token contracts.
- Require transparent signers: publish wallet addresses and require multiple, independent signers per transaction.
- Implement emergency stop mechanisms: add pausability or emergency brakes for critical functions.
How should projects respond immediately after a breach?
Containment steps include freezing affected contracts where possible, coordinating with exchanges to flag suspect deposits (if contact channels exist), publishing a full postmortem, deploying an audited replacement contract and restoring community trust through transparent communication.
Frequently Asked Questions
How many UXLINK tokens were minted during the attack?
Initial reports indicate about 2 billion tokens were minted early in the attack; some security firm estimates suggest the attacker may have created up to nearly 10 trillion tokens, depending on how the exploit was executed.
Can timelocks and caps fully stop minting exploits?
Timelocks and hard-coded caps greatly reduce risk but must be combined with secure multisig configurations, independent audits and operational transparency to form a robust defense-in-depth strategy.
Key Takeaways
- UXLink exploit: a multisig delegate call vulnerability enabled mass minting and a severe price collapse.
- Technical fixes: deploying audited contracts, removing mint functions and hard-coding supply limits are essential.
- Operational best practices: timelocks, renounced privileges, independent audits and transparent governance restore security and trust.
Conclusion
The UXLink exploit illustrates how a single multisignature vulnerability can undermine a token ecosystem. Prioritizing smart contract security, implementing timelocks, hard-coded caps and ongoing audits will better protect projects and communities. COINOTAG recommends projects adopt layered defenses and publish clear post-breach remediation steps.
Published: 2025-09-24 | Updated: 2025-09-24 | Author: COINOTAG
